Privacy by Design is a foundational tenet of modern IT, risk management, and cybersecurity practices that requires privacy to be incorporated into systems and technologies by default. Rather than retroactively addressing privacy concerns resulting from new technologies, business processes, or disruptions, a Privacy by Design approach dictates that privacy be embedded into the initial development or conception of organizational decisions.
Privacy by Design supports:
- Regulatory and legal compliance.
- Reputational and financial security.
- A privacy-forward, risk-aware operational culture.
- Proactive posture to legislative and cyber curves.
- Systematic, principled internal standards
- Cost-effective privacy risk management
Privacy is thus an innate, mandatory feature that’s baked into all digital transformations with the goal of mitigating, among other things, undue risk related to:
- Cyber attacks.
- Regulatory noncompliance.
- Class action lawsuits.
- Unsecured third-party services.
- Insider threats.
Privacy by Design: 7 Foundational Principles
The benefits of Privacy by Design materialize if the model is truly adopted.
The challenge, though, is standardizing and implementing lofty data protection objectives against shifting cybersecurity considerations, mass technology disruption, and the realities of enforcing business processes.
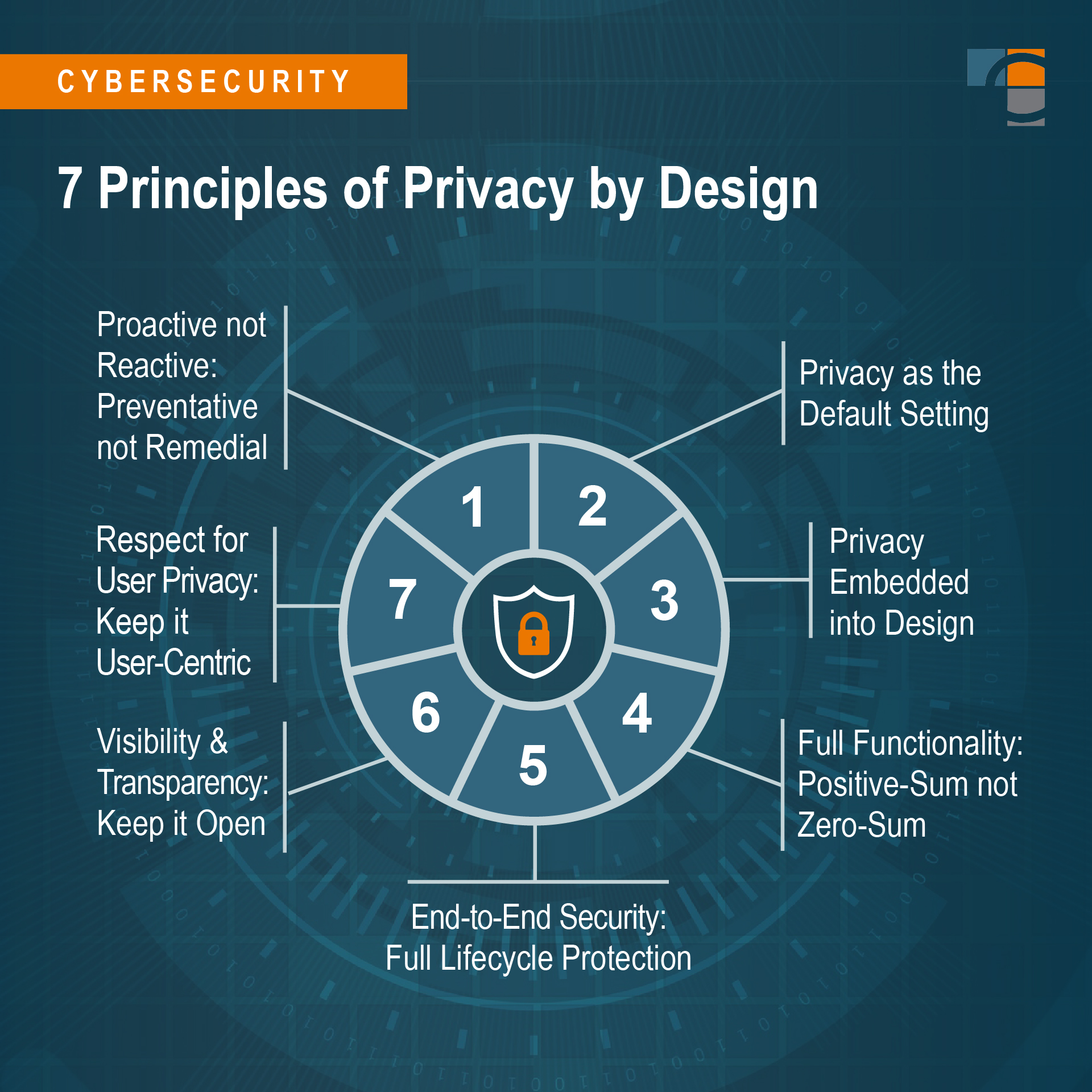
The design principles are codified in seven standards:
- Proactive not Reactive; Preventative not Remedial
- Privacy as the Default Setting
- Privacy Embedded into Design
- Full Functionality – Positive-Sum not Zero-Sum
- End-to-End Security – Full Lifecycle Protection
- Visibility and Transparency – Keep it Open
- Respect for User Privacy – Keep it User-Centric
These principles address a number of common challenges organizations face when deploying new applications or business systems, such as:
- Rigid privacy requirements create more friction and a less desirable working environment. Employees, customers, vendors, and users will find it difficult to comply with data privacy standards if doing so is cumbersome. User experience must be part of the conversation. Steep tradeoffs should not be made in a zero-sum game; all interests, outcomes, and functionality should be factored in as equally important.
- Universal enforcement of privacy requirements across all levels of the business, even exceeding regulatory requirements. If certain business units or hierarchical stakeholders play by different data protection rules, it’s less likely that global adherence can be achieved without animosity or failure. The minimum threshold of data protection at the company should be followed by all actors, and, even in the case of a privacy event, should not fall below compliance requirements.
- Cradle-to-grave data security and data privacy. As data flows between systems and lines of business, there can’t be security or accountability gaps. The full lifecycle of data must be managed consistently and at certain points along the way encrypted, logged, or destroyed.
Privacy by Design aims to maximize the incorporation of privacy protections while minimizing or reframing any perceived downsides.
Whether it’s GDPR, CCPA, HIPAA, PCI-DSS, or SOX, Privacy by Design enables organizations to build frameworks and coalitions around compliance and audit readiness.
Establishing a Data Protection Culture
Privacy by Design has influenced subsequent iterations and applications of “value-sensitive design,” meaning the placement of certain values or ethics at the forefront of process engineering. This includes new models for Data Protection by Design, further heightening the demand and adoption of stringent information security practices.
Privacy concerns aren’t going away; Big Data isn’t retreating. Organizations must create a comprehensive culture around risk, security, and privacy. They must institute strong privacy defaults throughout all facets of the business, inclusive of people, processes, and technology.
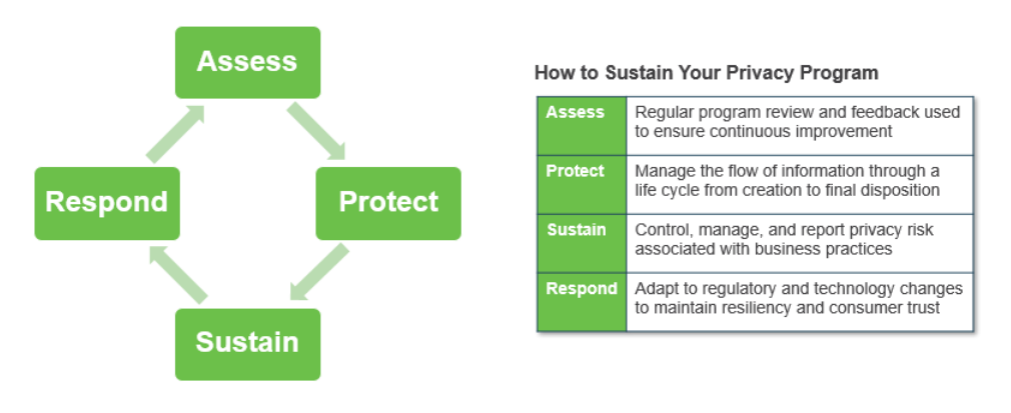 To start, consider:
To start, consider:
- Privacy champions or privacy ambassadors within the cyber unit and embedded into other teams.
- Internal education initiatives paired with external counsel and training.
- Documented governance and vendor management protocols.
- A combination of manual and automated data inventory management and hygiene.
- Routine industry-, data-, and geography-specific risk assessments.
- Implementation of the National Institute of Standards and Technology (NIST) Privacy Framework assessment.
- Leveraging regulatory crosswalks and risk control families.
- Privacy Impact Assessment (PIA) and Data Protection Impact (DPIA) assessment.
Research from MIT shows that the technology for data privacy (also known as privacy-enhancing technologies) is innovating faster than almost any other form of technology on the market, improving 178% annually. Clearly, the demand for data privacy protection exists on both the consumer and commercial side.
Beginning with the seven foundational principles of Privacy by Design, your organization can architect a culture that protects personal data, respects data collection boundaries, optimizes against privacy risk, and complies with all relevant laws.
To learn more, contact the cyber and privacy security experts at CrossCountry Consulting.